Abstract
An optimization approach based on Cuckoo Search (CS) algorithm is proposed for structural local damage detection in this study. The nonlinear objective function for the damage identification problem is established by using the natural frequencies and modal assurance criteria (MAC). The CS algorithm is presented to solve the objective function. A dual-span continuous beam and a truss structure are studied as numerical example to illustrate the correctness and efficiency of the propose method. Meanwhile, a laboratory work is conducted for further verification. The simulation and experiment results show that the CS algorithm can identify the local structural damages effectively even under measurement noise. The advantage of the present method is that only the first few natural frequencies and mode shapes are needed in the identification.
1. Introduction
Structural damage detection research is an active area in the field of structural health monitoring. Negligence of the local damages may cause serious engineering problems. Various approaches for damage detection have been studied and accepted by the industry and regulatory agencies. Specially, in the last few decades, non-destructive approaches like techniques based on vibration response for damage identification have been widely studied.
Previous studies have shown that the associated changes in the structures will result in changes in the natural frequencies, mode shapes, modal strain energies, damping ratios, or other dynamic characteristics of the system. Therefore, detecting some of these properties of the damaged structure, the location and extent of the local damage could be identified. Extensive literature reviews on vibration-based damage detection techniques have been reported. Cawley et al. (1979) [1] and Narkis et al. (1994) [2] identified the structure damage by using measured natural frequencies. Then by applying the curvature mode shapes, Ghafory et al. (2013) [3] and Wang et al. (2013) [4] localized the local damages effectively. And Yang et al. (2011) [5] utilized the modal flexibility to damage detection.
Excepting numerous studies in frequency domain, damage detection methods in time domain have been developed rapidly. By utilizing the features of dynamic response sensitivity, Lu et al. (2007) [6] proposed a response sensitivity-based method to identify structural damage effectively. Besides, Fu et al. (2013) [7], Law et al. (2010) [8] and Lu et al. (2013) [9] have done their job in time domain.
In recent years, with the development of the computer technique and mathematics, swarm intelligence technique gained its popularity. By transferring the local damage identification problem to the objective function optimizing, the damage can be obtained by minimizing the objective function formulated of the difference between the measured and the calculated data from the certain structural system. Wu et al. (1992) [10] applied the Neural network (NN) for damage detection. Besides, genetic algorithm (GA) as a global optimization method has been used byBuezas et al. (2011) [11] and Chou et al. (2001) [12] for structural damage detection. Then some new optimization algorithms such as artificial fish-school swarm algorithm utilized by Luo et al. (2007) [13], colony optimization (ACO) used by Yu et al. (2011) [14] and used particle swarm optimization (PSO) applied by Guo et al. (2014) [15] have been introduced in damage detection. But these swarm intelligence techniques both have common failing on slow convergence and easy to fall into local optimization.
Recently, a new swarm intelligence calls Cuckoo search algorithm (CS) has been developed by Yang et al. (2010) [16] for numerical optimization problems, inspired by the reproduction strategy of cuckoos, which is utilized increasingly for its feasibility and efficiency.
The CS is simple in concept and has less parameter to adjust and is easy to implement. It has been applied in many areas like constrained optimization problems and multi-objective optimization problems. Walton et al. (2011) [17] modified the CS to reach high convergence to the global minimum problem even at high numbers of dimensions. Yang et al. (2013) [18] utilized the CS to solve multi-objective design optimization. Wen et al. (2014) [19] modified cuckoo search algorithm based on Solos and Wets local search technique and the method is proposed for constrained global optimization that relies on an augmented Lagrangian function for constraint-handling.
So far, very few studies have been done on structural damage detection based on CS algorithm. In this paper, we discuss the damage detection for structural components based on CS algorithm. Besides numerical simulations, laboratory work is carried out to further validate the effectiveness of the present method. In the identification, only the first few natural frequencies and/or mode shapes are needed. Results show that local structural damages can be identified successfully even under measurement noise, which shows that CS algorithm is very promising for damage detection.
2. A brief introduction to Cuckoo search algorithm
The CS method is becoming very popular due to its simplicity, efficiency, and fast convergence properties. Firstly, introduce the cuckoo search algorithm. Cuckoo search algorithm is inspired by the cuckoo search for host nests to breed. At the most basic level, cuckoos lay their eggs in the nests of other host birds, which may be of different species. The host bird may discover that the eggs are not it’s own and either destroy the egg or abandon the nest all together. This has resulted in the evolution of cuckoo eggs which mimic the eggs of local host birds. For simplicity, we use the following three idealized rules:
1) Each cuckoo lays one egg at a time, which represents a set of solution co-ordinates, and dumps it in a randomly chosen nest;
2) The best nests with high quality of eggs (solutions) will carry over to the next generations;
3) The number of available host nests is fixed, and a host can discover an alien egg with a probability . In this case, the host bird can either throw the egg away or abandon the nest so as to build a completely new nest in a new location.
For simplicity, this last assumption can be approximated by a fraction of the nests being replaced by new nests (with new random solutions at new locations). For a maximization problem, the quality or fitness of a solution can simply be proportional to the objective function.
Based on these three rules, the basic steps of the Cuckoo Search (CS) can be summarized as flee shown in Fig. 1.
When generating new solutions for, say Cuckoo , a Levy flight in performed:
where is the step size which should be related to the scales of the problem. In most cases, we can use. The product means entry-wise multiplications. Levy flight essentially provide a random walk while their random steps are drawn from a Levy distribution for large steps:
which has an infinite variance with an infinite mean. Here the consecutive jumps/steps of a cuckoo essentially form a random walk process which obeys a power-law step-length distribution with a heavy tail.
In addition, a fraction of the worst nests can be abandoned so that new nests can be built at new locations by random walks and mixing. The mixing of the eggs/solutions can be performed by random permutation according to the similarity/difference to the host eggs.
Obviously, the generation of step size samples is not trivial using Levy flights. A simple scheme discussed in detail by Yang et al. (2010) [20] can be summarized as:
where and are drawn from normal distributions. That is:
with:
here is the standard Gamma function.
When generating a new egg in Fig. 1, a Levy flight is performed starting at the position of a randomly selected egg, if the objective function value at these new coordinates is better than another randomly selected egg then that egg is moved to this new position. The scale of this random search is controlled by multiplying the generated Levy flight by a step size. Yang et al. (2009) [21] do not discuss boundary handling in their formulation, but an approach similar to PSO boundary handling is adopted here. When a Levy flight results in an egg location outside the bounds of the objective function, the fitness and position of the original egg are not changed.
Fig. 1The flowchart of the CS algorithm
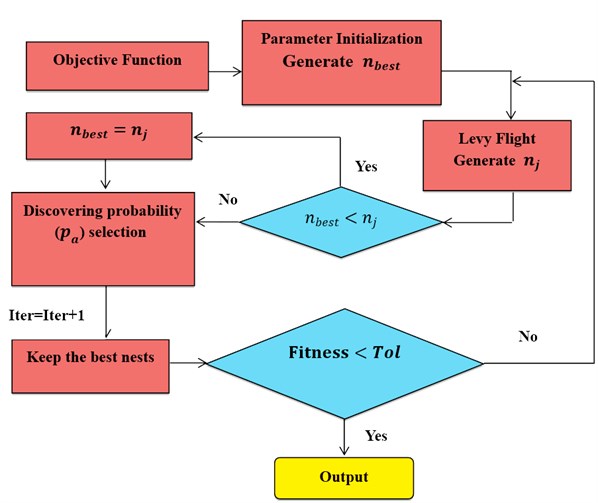
Above all, by using Levy flight and fraction , CS algorithm can be proposed to various optimization problems effectively and show a high convergence rate to the trace global minimum. In this paper, CS algorithm is selected to solve the damage index objective function of the engineering structure. And then we can conclude the location and extent of the damaged structures to carry out the structural damage detection. And we choose frequency residual error and modal assurance criteria (MAC) to build up the structural objective function as below.
3. Methodology for vibration-based damage identification
The premise for techniques based on vibration responses is that damage causes a change in structural physical properties, mainly in stiffness and damping at the damaged locations.
3.1. Modeling structural local damage
The eigenvalue equation for a finite element model of the system is:
where and are the structural mass matrix and stiffness matrix, respectively. And is the th natural frequency and is the corresponding mode shape.
In the finite element model of the damaged system, the local damage is modeled as reduction in the elemental stiffness of the system, but the other properties remain unchanged.
When a structure with elements is damaged, the reduction of the stiffness can be evaluated by a set of damage parameters . The value range of parameter is between 0 and 1.When 1, means that the th element is intact while , it represents that system is completely damaged. And then the stiffness matrix of the damaged system can be written as:
where is the stiffness matrix of the damaged system, and presents the th elemental stiffness matrix in the global form. Damage identification implies to identify each value in the damage parameter vector , based on the damage model mentioned above.
3.2. Objective function based on vibration data
It is well known that the changes of stiffness will cause the changes of the structural properties, such as natural frequencies and mode shapes. In this study, the objective function for damage detection is based on vibration data, such as natural frequencies and mode shapes. By minimizing the differences between the measured response data and the calculated one, we can locate and quantify the local damage of the certain system.
Considering the mode shape data, modal assurance criteria (MAC) proposed by Brehm et al. (2010) [22] is utilized. The is expressed as:
where and are the th calculated and measured mode shapes, respectively.
Based on and taking into account the changes both in natural frequencies and mode shapes, the objective function used for damage detection is expressed as:
where is the modal order, , , , is the th order frequency and mode shape of the intact and damaged system. Besides, the Eq. (9) mentioned above is:
As described above, the value range of the damage parameter is between 0 and 1. When , means that the th element is intact while , it represents that system is completely damaged. Then the objective function can be:
If the value of damage parameter vector matches the given particular damage condition, the objective function will achieve its minimum value 0. In other words, when the minimum value of the objective function is identified, the corresponding parameter vector will indicate damage status of the structure. Then based on the value of the identify parameters , we can find out the local damages of the system.
4. Numerical simulations
To evaluate the performance of the certain method we carried out some simulations and a practical experimentation.
4.1. Parameters setting for Cuckoo search algorithm
The parameter of discovery rate of alien eggs/solutions is taken as 0.25. The searching step is taken as 1. The initial fitness of the objective function is 100. The tolerance of the iteration is set to be 1e-7. To include the uncertainty in the measured data and to study the sensitivity of CS to noise, uniformly distributed random noise is added to measured data in the simulation. To simulate measurement noise, the natural frequencies are contaminated with 1 % noise and 3 % noise is added to the modal displacement proposed by Kang et al. (2012) [23] for all the cases.
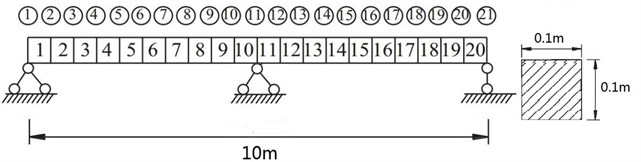
Fig. 2A dual span supported beam and cross section
4.2. A dual span simply supported beam
A dual span simply supported beam is studied as an example. Fig. 2 illustrates the geometric characteristics of the beam. The total number of elements and nodes are 20 and 21, respectively. Young’s modulus of the system is 210 GPa, mass density is 7.8×103 kg/m3, the beam length is 10 m. The damage case is studied and the first 3 natural frequencies and modes shapes are utilized.
In this case it is assumed that element 5 have both 10 % reduction in stiffness meanwhile element 6 has 15 %, element 16 has 20 %, respectively. And element 5 and element 6 are two adjacent elements. We consider both the conditions with and without noise. Damage detection results are shown in Fig. 3. In noise-free condition, the identified results from CS algorithm converge to the true value with the final fitness value less than 10-8. In noise-contaminated condition, their final converged fitness value is 9.2745×10-8. It indicates that the identified results are close to the true damage status of the structure. The curves of fitness values for CS are demonstrated in Fig. 4, one can find that CS leads to convergence rapidly. The evolutionary processes of damaged element in noise-contaminated condition are shown in Fig. 5, proving all the damaged elements can be found correctly. What needed to be emphasized is that all these data were collected 20 times for average.
Fig. 3Damage identification result of the dual span supported beam
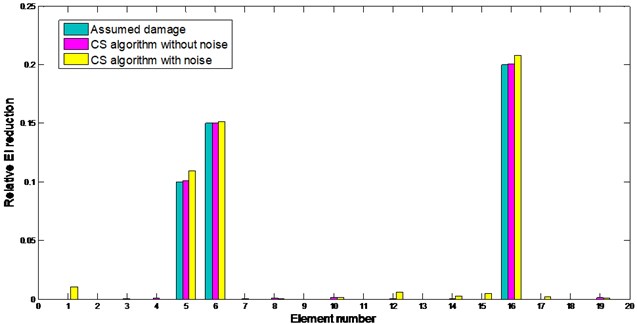
Fig. 4The iteration process of objective function based on CS algorithm for the simply supported beam
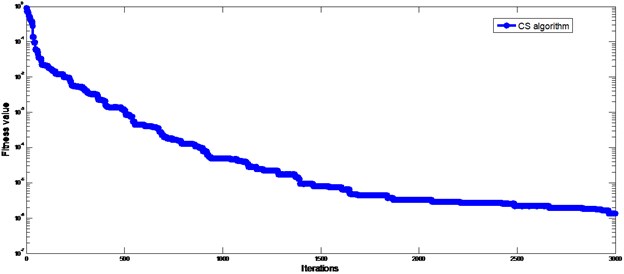
Fig. 5Evolutionary processes of damage indices of the beam
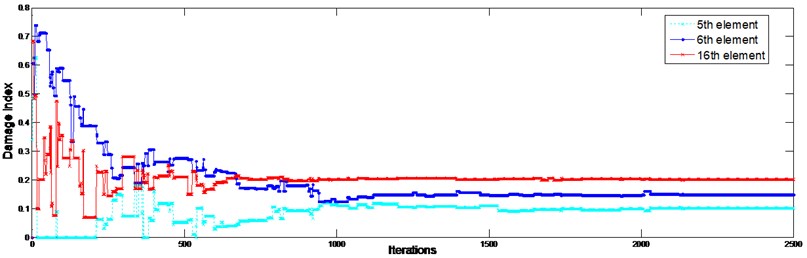
Table 1Damage cases and relative errors for damage identification of the beam
Damage case | Element | Identified result (%) | True value (%) | Relative error (%) |
Case 1 | 16 | 20.16 | 20 | 0.16 |
6 | 14.96 | 15 | 0.04 | |
5 | 9.76 | 10 | 0.24 | |
1* | 1.08 | 0 | 1.08 | |
12* | 0.62 | 0 | 0.62 | |
* denotes false alarms | ||||
Relative errors in this case are listed in Table 1. Three damaged elements are identified accurately. This case illustrates the robustness and effectiveness of the proposed method.
4.3. A truss structure
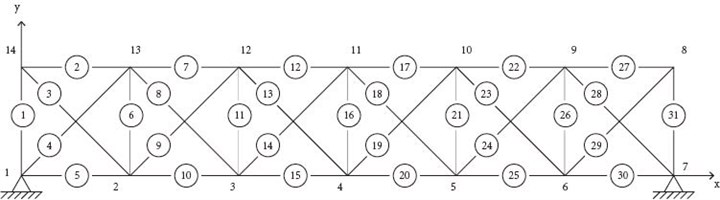
A 31-bar truss structure shown in Fig. 6 is studied as another example. The length of each exterior bar is 1 m, and length of interior bar is 1.41 m. The section area of each bar is 0.004 m2. Young’s modulus is 200 GPa, and mass density 7800 kg/m3. Total numbers of elements and nodes are 31 and 14, respectively.
Fig. 6A 31-bar truss structure
The first six frequencies and mode shapes are utilized in this case. Three local damages are assumed to locate at the 3th, 8th, 14thand 28th elements, with a reduction of stiffness of 10 %, 12 %, 15 %, and 20 %, respectively. The identified results are shown in Fig. 7 for both noise-free and noise-contaminated conditions. Damages have been identified accurately in both aspects of location and extent when noise is free. In noise condition, damage locations have been correctly detected with only little false alarms. The identification errors are listed in Table 2. Fig. 8 shows the evolution processes of all damaged indices in noise condition. The evolutionary processes of damaged element in noise-contaminated condition are shown in Fig. 9. What needed to be stressed is that all these data were collected 20 times for average. Results show that the proposed method is efficient on determining the sites and the extents of the structure damages.
Fig. 7Damage identification result of the truss
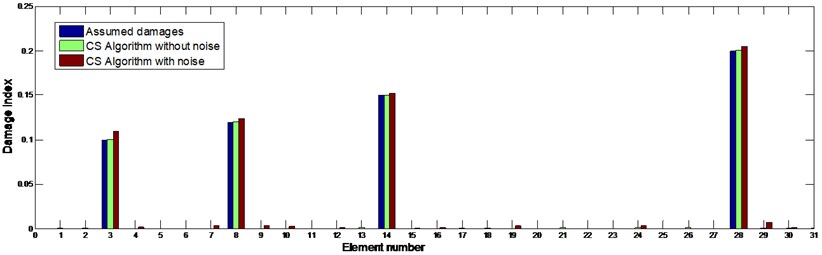
Fig. 8Iteration process of objective function based on Cuckoo search algorithm for the truss
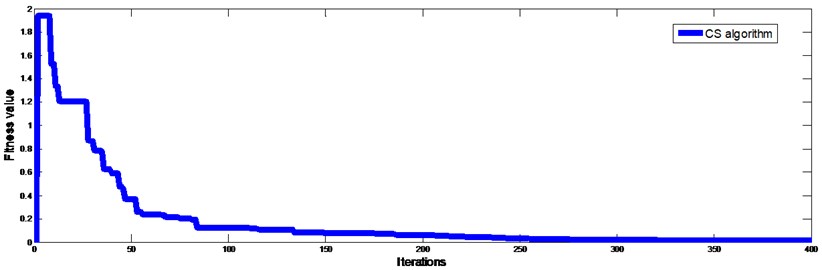
Fig. 9Evolutionary processes of damage indices of the truss
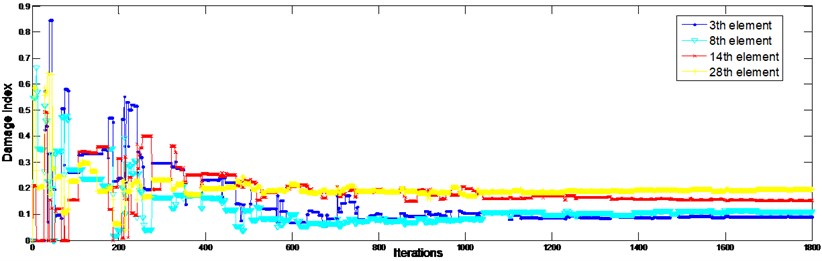
Table 2Damage cases and relative errors for damage identification of the truss
Element | Identified result (%) | True value (%) | Relative error (%) |
14 | 15.19 | 15 | 0.19 |
28 | 20.08 | 20 | 0.08 |
3 | 9.53 | 10 | 0.47 |
8 | 12.14 | 12 | 0.14 |
7* | 0.35 | 0 | 0.35 |
9* | 0.32 | 0 | 0.32 |
24* | 0.4 | 0 | 0.4 |
28* | 0.68 | 0 | 0.68 |
* denotes false alarms | |||
5. Laboratory work
The proposed method is further demonstrated with laboratory results from a free-free steel beam as shown in Fig. 10. The beam is hung by two nylon ropes at two ends. The parameters of the beam are: length 2.1 m, width 0.025 m and height 0.019 m, the Young’s modulus and mass density of the material are 207 GPa and 7832 kg/m3, respectively. The damage is simulated by a crack located at 1.72 m from the left free end, created by a machine saw with 1.3 mm thick cutting blade. The crack depth is 3 mm. An impulsive force was applied with an impact hammer model B&K 8202 at 1.2 m from the left end. The sampling frequency is 2000 Hz. Four-second acceleration response data collected by an accelerometer model B&K 4370 at the mid-span of the beam are used to extract the first five natural frequencies of the intact and damaged beam for damage identification. The first 5 natural frequencies of the intact and the damaged beam with crack are shown in “*” denotes false alarms.
Fig. 10Sketch of the experimental beam (dimensions are not scaled)

The beam is discretized into twenty Euler beam elements with two degrees-of-freedom at each node. The crack locates at the 17th element in the finite element model. The natural frequencies calculated from the finite element model are quite close to the measured values, indicates that the initial finite element model is accurate enough for the subsequent damage identification.
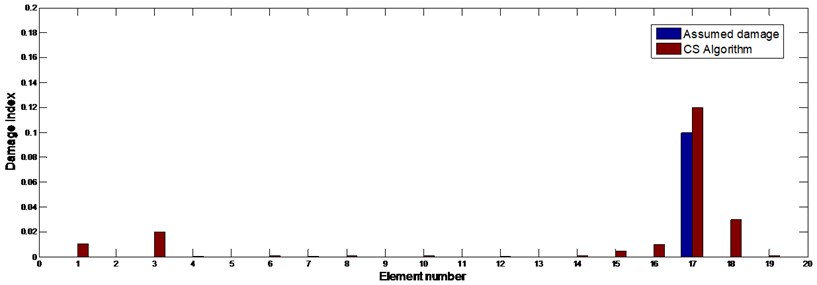
As only the measured natural frequency data are used in the damage identification, the first term in the objective function Eq. (10) is used and second term removed by setting . Fig. 11 shows the identified result. One can find that the location of the damage has been identified successfully, and the identified extent of damaged element 17 is 12.3 %. The true damage value is obtained by a direct identification using the measured and calculated natural frequencies with the known location of damaged element, i.e. the 17th element, and other elements are intact. It is found to be 9.5 %. By observing Fig. 13, it is found there are 2 large false identifications in element 3 and 18. The false alarm in element 3 may due to the reason that it is the symmetric one of element 17. The false alarm in element 18 can be explained since element 18 is in immediate adjacent to the damage and the vibration energy in the element would be much more disturbed than those in other elements as discussed by Shi et al. (2000) [24]. The natural frequencies of the beam calculated with the identified parameters are shown in Table 3 and they are found matching the experimental values very well indicating the success of the identification.
Fig. 11Iteration process of objective function based on Cuckoo search algorithm for the experimental beam
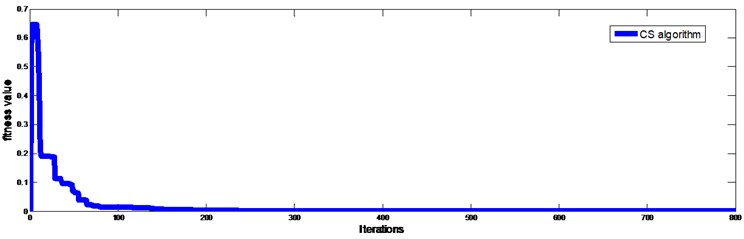
Fig. 12Evolutionary processes of damage indices for the experimental beam
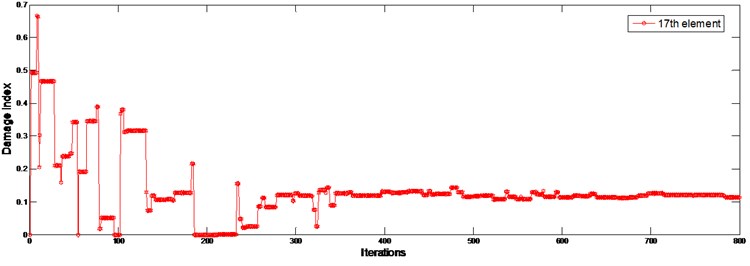
Fig. 13Damage identification result of the experimental beam
6. Conclusions
A damage detection approach based on CS algorithm using modal data is proposed. The numerical simulation results from a continuous beam, a truss structure and a laboratory work illustrate that the present approach is correct and efficient for detecting structural local damages. The proposed method only needs the first few natural frequencies and mode shapes of the structure in the identification. The present method is not sensitive to measurement noise.
Table 3Modal frequencies of beam from test and analytical results
Modal frequency | 1st | 2nd | 3rd | 4th | 5th | |
Intact | Measured | 22.50 | 62.75 | 123.00 | 203.25 | 303.50 |
FEM | 22.75 (0.25) | 62.80 (0.05) | 123.50 (0.50) | 203.50 (0.25) | 304.00 (0.50) | |
Damage | Measured | 22.80 | 62.50 | 122.50 | 202.50 | 302.50 |
CS | 22.75 (0.25) | 62.55 (0.05) | 122.00 (0.50) | 202.25 (0.25) | 302.75 (0.25) | |
A(b) is form of data (relative error) | ||||||
References
-
Cawley P., Adams R. D. The location of defects in structures from measurements of natural frequencies. Journal of Strain Analysis, Vol. 14, Issue 2, 1979, p. 49-57.
-
Narkis Y. Identification of crack location in vibrating simply supported beams. Journal of Sound and Vibration, Vol. 172, Issue 4, 1994, p. 549-558.
-
Ghafory M., Ghasemi M. System identification method by using inverse solution of equations of motion in frequency domain. Journal of Vibration and Control, Vol. 19, Issue 11, 2013, p. 1633-1645.
-
Wang S. S., Ren Q. W., Qiao P. Z. Structural damage detection using local damage factor. Journal of Vibration and Control, Vol. 12, Issue 9, 2006, p. 955-973.
-
Yang Q. W. A new damage identification method based on structural flexibility disassembly. Journal of Vibration and Control, Vol. 17, Issue 7, 2011, p. 1000-1008.
-
Lu Z. R., Law S. S. Features of dynamic response sensitivity and its application in damage detection. Journal of Sound and Vibration, Vol. 303, Issue 1, 2007, p. 305-329.
-
Fu Y. Z., Lu Z. R., Liu J. K. Damage identification in plates using finite element model updating in time domain. Journal of Sound and Vibration, Vol. 332, 2013, p. 7018-7032.
-
Law S. S., Zhang K., Duan Z. D. Structural damage detection from coupling forces between substructures under support excitation. Engineering Structures, Vol. 32, Issue 8, 2010, p. 2221-2228.
-
Lu X. B., Liu J. K., Lu Z. R. A two-step approach for crack identification in beam. Journal of Sound and Vibration, Vol. 332, Issue 2, 2013, p. 282-293.
-
Wu X., Ghaboussi J., Garrett J. H. Use of neural networks in detection of structural damge. Computers and Structures, Vol. 42, 1992, p. 649-659.
-
Buezas F. S., Rosales M. B., Filipich C. P. Damage detection with genetic algorithms taking into account a crack contact model. Engineering Fracture Mechanics, Vol. 78, Issue 4, 2011, p. 695-712.
-
Chou J. H., Ghaboussi J. Genetic algorithm in structural damage detection. Computers and Structures, Vol. 79, Issue 14, 2001, p. 1335-1353.
-
Luo Y., Zhang J. T., Li X. X. The optimization of PID controller parameters based on artificial dish swarm algorithm. Proceedings of the IEEE International Conference on Automation and Logistics, 2007, p. 1058-1062.
-
Yu L., Xu P. Structural health monitoring based on continuous ACO method. Microelectronics Reliability, Vol. 51, Issue 2, 2011, p. 270-278.
-
Guo H. Y., Li Z. L. Structural damage identification based on evidence fusion and improved particle swarm optimization. Journal of Vibration and Control, Vol. 20, Issue 9, 2014, p. 1279-1292.
-
Yang X. S., Deb S. Engineering optimization by Cuckoo Search. International Journal of Mathematical Modelling and Numerical Optimisation, Vol. 1, Issue 4, 2010, p. 330-343.
-
Walton S., Hassan O., Morgan K., Brown M. R. Modified cuckoo search: A new gradient free optimization algorithm. Chaos, Solitons and Fractals, Vol. 44, 2011, p. 710-718.
-
Yang X. S., Deb S. Multi-objective cuckoo search for design optimization. Computer and Operations Research, Vol. 40, 2013, p. 1616-1624.
-
Wen L., Liang X. M., Huang Y. F., Chen Y. X. An effective hybrid cuckoo search algorithm for constrained global optimization. Neural Computing and Applications, Vol. 25, 2014, p. 991-926.
-
Yang X. S. Engineering Optimization: an Introduction with Metaheuristic Applications. John Wiley and Sons, 2010.
-
Yang X. S., Deb S. Cuckoo search via Levy flights. Proceedings of World Congress on Nature and Biologically Inspired Computing, 2009, p. 210-214.
-
Brehm M., Zabel V., Bucher C. An automatic mode pairing strategy using an enhanced modal assurance criterion based on modal strain energies. Journal of Sound and Vibration, Vol. 329, 2010, p. 5375-5392.
-
Kang F., Li J. J., Xu Q. Damage detection based on improved particle swarm optimization using vibration data. Applied Soft Computing, Vol. 12, Issue 8, 2012, p. 2329-2335.
-
Shi Z. Y., Law S. S., Zhang L. M. Structural damage detection from modal strain energy change. Journal of Engineering Mechanics, ASCE, Vol. 126, Issue 12, 2000, p. 1216-1223.
About this article
This work is supported by the National Natural Science Foundation of China (11172333, 11272361), Doctoral Program Foundation of Ministry of Education of China (20130171110039), and the Guangdong Province Science and Technology Program (2012A030200011). Such financial aids are gratefully acknowledged.
